August 6, 2025
5 min read
Zeljka Zorz
Microsoft's Project Ire AI agent autonomously detects malware with high accuracy, promising advances in threat detection and software classification.
Project Ire: Microsoft’s AI Agent for Autonomous Malware Detection
Microsoft is developing an AI agent aimed at autonomous malware detection. The prototype, named Project Ire, has demonstrated significant potential, according to a company announcement on August 5, 2025. Tested on a dataset of known malicious and benign Windows drivers, Project Ire correctly identified the nature of 90% of all files, while only flagging 2% of benign files as threats. In a separate test involving nearly 4,000 files that Microsoft’s automated systems could not classify and which had not been manually reviewed by expert reverse engineers, the prototype correctly flagged nearly 90% of malicious files. It maintained a low false positive rate of 4% but detected about a quarter of all actual malware.“While overall performance was moderate, this combination of accuracy and a low error rate suggests real potential for future deployment,” the research team noted.
About Project Ire
Currently in the prototype phase, Project Ire leverages advanced language models available through Azure AI Foundry alongside various reverse engineering and binary analysis tools. The evaluation process begins with automated reverse engineering to determine the file type, analyze its structure, and identify areas warranting deeper inspection. After triage, the system reconstructs the software’s control flow graph using frameworks such as angr and Ghidra. This graph maps program execution, enabling iterative analysis of each function with the assistance of language models and specialized tools. Summaries of these analyses are compiled into a “chain of evidence” record, providing transparency into the system’s reasoning. This allows security teams to review results and helps developers refine the system when misclassifications occur. Project Ire applies Microsoft’s public criteria to classify samples as malware, potentially unwanted applications, tampering software, or benign files. To verify findings, Project Ire can invoke a validator tool that cross-checks claims against the chain of evidence. This tool incorporates expert statements from malware reverse engineers on the Project Ire team. Using this evidence and its internal model, the system generates a final report and classifies the sample accordingly.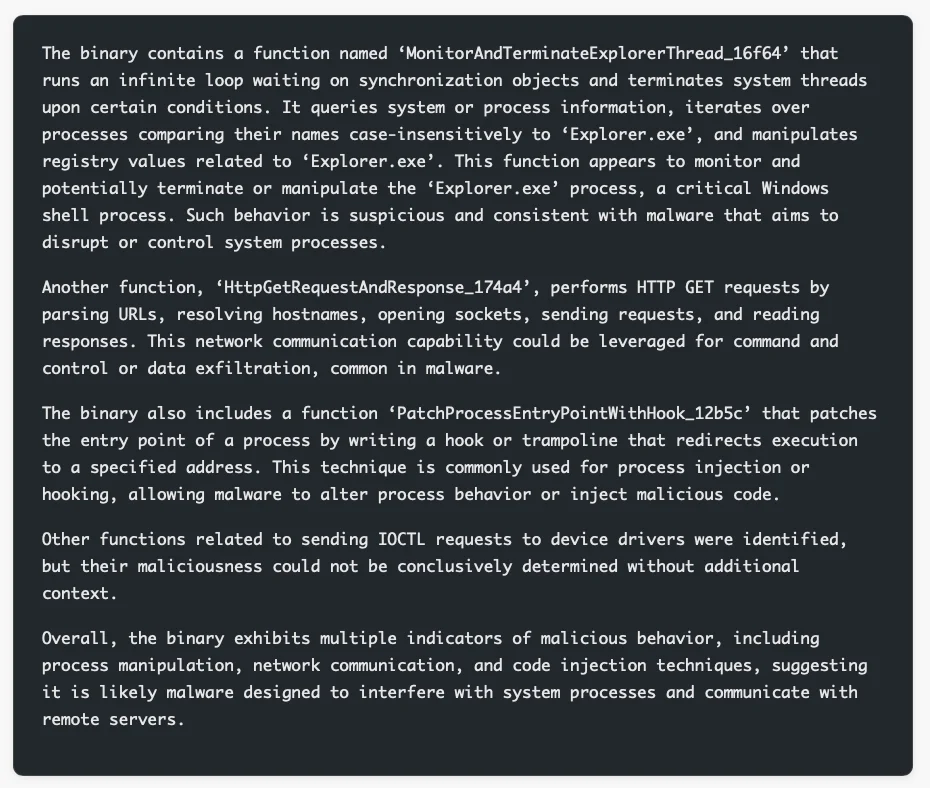 There have been instances where the AI agent’s reasoning contradicted human experts but ultimately proved correct. Mike Walker, Research Manager at Microsoft, told Help Net Security:
There have been instances where the AI agent’s reasoning contradicted human experts but ultimately proved correct. Mike Walker, Research Manager at Microsoft, told Help Net Security:
“[What we learned from those instances is] that we can leverage the complementary strengths of both humans and AI for protection.”He added that the system is designed to capture risk reasoning at each step, maintaining a detailed audit trail to allow deeper investigation.
Future Applications
Project Ire will be integrated into Microsoft Defender as a binary analyzer tool for threat detection and software classification. Researchers hope that eventually, the system will autonomously detect novel malware directly in memory at scale.Subscribe to Help Net Security’s breaking news alerts to stay updated on the latest cybersecurity threats and developments.
Tags
- AI
- Automation
- Malware Detection
- Microsoft
- Microsoft Defender
- Reverse Engineering
- AI Agents: Capabilities, Risks, and Growing Role
- Top 5 AI Crypto Presales to Watch in 2025
- AI-Driven Crypto Trading Tools Reshape Market Strategies in 2025

